The Single Strategy To Use For Aws S3 Backup
Wiki Article
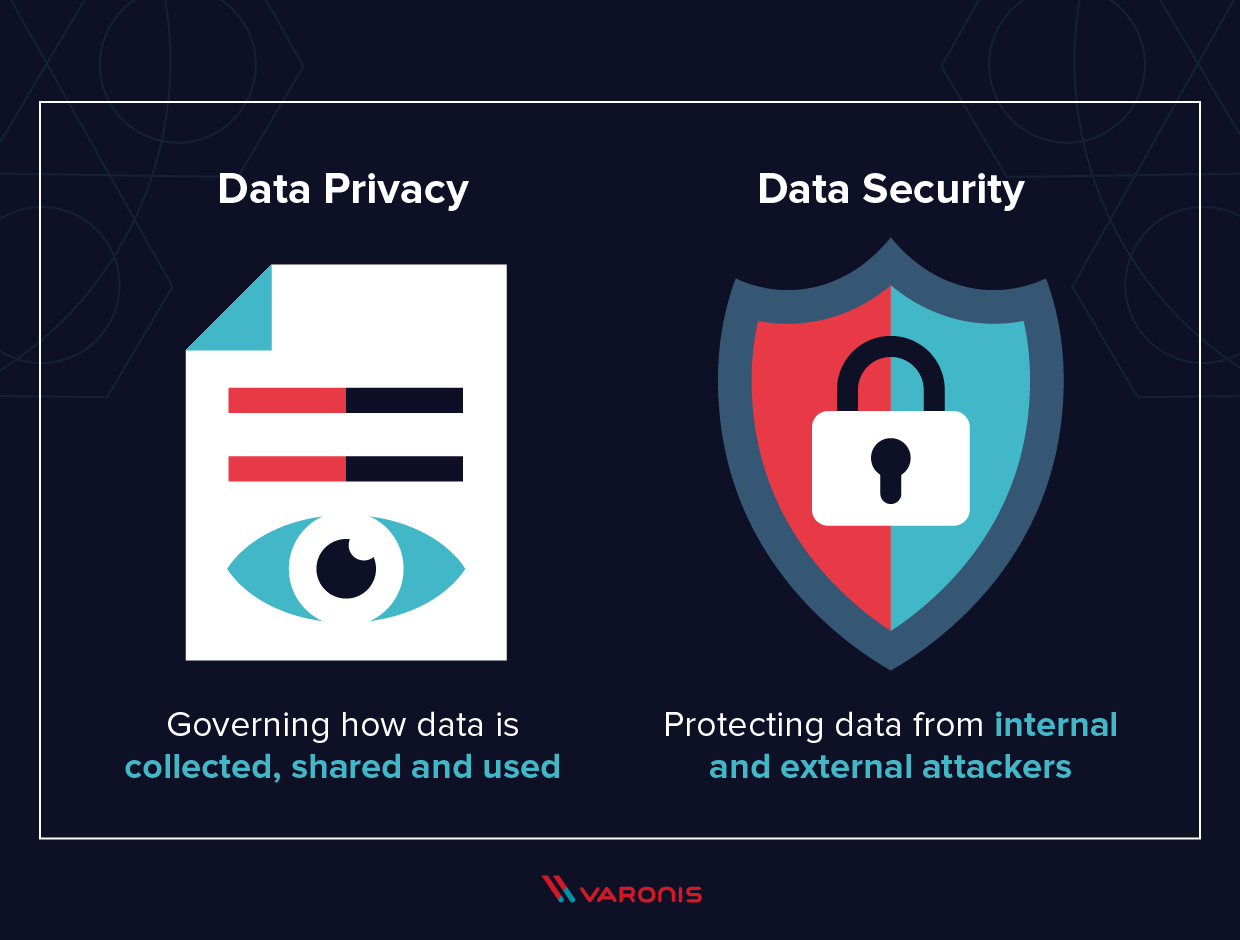
The Best Strategy To Use For Protection Against Ransomware
Table of ContentsThe 8-Minute Rule for Protection Against RansomwareThe Buzz on Ransomware ProtectionThe Ultimate Guide To S3 BackupSome Known Details About Ransomware Protection Indicators on S3 Backup You Need To KnowA Biased View of S3 Backup
Data protection is the procedure of protecting essential information from corruption, concession or loss - https://folkd.com/user/clumi0. The value of information security boosts as the amount of data produced and also stored remains to expand at unprecedented prices. There is additionally little tolerance for downtime that can make it difficult to accessibility crucial info.Securing information from concession and also ensuring data personal privacy are various other key components of data security. The coronavirus pandemic triggered countless workers to function from home, resulting in the need for remote data protection (http://aulavirtual.cali.edu.co/index.php/comunicacion/foro/clumio-1). Organizations must adapt to ensure they are protecting data any place staff members are, from a central data center in the workplace to laptop computers at house.
The key principles of data defense are to safeguard and also offer data under all conditions. The term data security defines both the functional backup of information as well as company continuity/disaster recovery (BCDR). Information security techniques are developing along two lines: data accessibility and also information monitoring. Information accessibility ensures individuals have the data they need to conduct service even if the information is damaged or shed.
Info lifecycle monitoring is a comprehensive method for valuing, cataloging and also securing details properties from application and user errors, malware as well as infection strikes, equipment failing or center blackouts and interruptions. More recently, data administration has come to include discovering methods to open organization worth from or else inactive duplicates of information for coverage, test/dev enablement, analytics and also various other objectives.
The 9-Minute Rule for Data Protection
Storage space photos can instantly produce a set of reminders to info saved on tape or disk, allowing faster data recuperation, while continuous data defense (CDP) backs up all the information in a business whenever a change is made. Information mobility-- the ability to relocate information amongst various application programs, calculating atmospheres or cloud solutions-- provides another collection of problems as well as solutions for information security.
Information was occasionally replicated, commonly each night, to a tape drive or tape collection where it would certainly sit till something went wrong with the main information storage space. That's when organizations would certainly access and also use the backup data to bring back shed or harmed information. Backups are no much longer a standalone feature.
What Does Aws Backup Do?
Backup and archiving, for example, have actually been treated as two different features. Back-up's purpose was to recover information after a failure, while an archive offered a searchable copy of information. However, that resulted in repetitive information collections. Today, some items back up, archive and index data in a single pass.
Snapshots and also replication have made it feasible to recuperate much faster from a calamity than in the past. When a server stops working, data from a backup variety is used instead of the main storage space-- however only if an organization takes steps to avoid that backup from being customized.
The original data from the backup range is after that utilized for reviewed operations, and also create operations are guided to the differencing disk. This method leaves the original back-up data unmodified. And also while all this is occurring, the fallen short server's storage is reconstructed, and also data is duplicated from the back-up selection to the fallen short web server's recently reconstructed storage - https://www.aeriagames.com/user/clumi0/.
The Greatest Guide To S3 Cloud Backup
Data deduplication, also referred to as information dedupe, plays a key role in disk-based back-up. Dedupe eliminates redundant duplicates of information to minimize the storage capacity required for back-ups. Deduplication can be developed right into back-up software program or can be a software-enabled function in disk libraries. Dedupe applications replace repetitive data blocks with reminders to special data copies.Deduplication began as an information protection modern technology as well as has moved right into primary information as an important feature to lower the amount of ability required for extra expensive flash media. CDP has concerned play a vital function in calamity healing, as well as it makes it possible for quick recovers of backup information. Continuous information protection allows organizations to roll back to the last excellent copy of a file or data source, decreasing the quantity of information lost in the instance of corruption or data deletion.
CDP can additionally get rid of the demand to keep numerous duplicates of data. Rather, organizations retain a single copy that's updated continuously as changes take place.
Simultaneous matching is one strategy in which information is created to a neighborhood disk and also a remote site at the exact same time. The compose is ruled out total up until a confirmation is sent from the remote site, making sure that both sites are always identical. Mirroring requires 100% ability overhead.
Fascination About S3 Backup

The expense of recovering from a media failure is the moment it takes to go back to a safeguarded state. Mirrored systems can return to a safeguarded state rapidly; RAID systems take much longer because they need to recalculate all the parity. Advanced RAID controllers don't have to review an entire drive to recuperate data when doing a drive restore.
Considered that many drives go for about one-third capability, smart RAID can lower healing times dramatically. Erasure coding is an alternate to sophisticated RAID that's often utilized in scale-out storage space settings. Like RAID, erasure coding uses parity-based information defense systems, writing both data and also parity throughout a cluster of storage nodes.
Replication is one more information defense choice for scale-out storage space, where information is mirrored from one node to another or to several nodes. Duplication is less complex than erasure coding, yet it eats at the very least twice the capacity of the protected data. With erasure coding, data is kept across different disks to safeguard against any type of single point of failing.
The Facts About Ec2 Backup Revealed
Most storage space systems today can track thousands of pictures without any substantial impact on efficiency. Storage systems making use of pictures can function with platforms, such as Oracle and also Microsoft SQL Server, to record a clean duplicate of data while the picture is occurring. This approach allows regular photos that can be stored for lengthy periods of time.With this technique, minimal data is lost as well as healing time is almost immediate. To secure against several drive failings or a few other major event, information facilities rely upon replication modern technology developed on top of photos. With snapshot duplication, just blocks of data that have actually transformed are copied from the main storage system to an off-site additional storage space system.
Report this wiki page